Ad hoc Network Security
The purpose of the project is to analyzes common security threats to MANET protocols, like Neighborhood Discovery Protocol (NHDP), OLSRv2, Simplified Multicast Forwarding (SMF), etc.
NHDP defines a HELLO messages exchange, enabling each NHDP Router to acquire topological information describing its 1-hop and 2-hop neighbors, and specifies information bases for recording this information.
An NHDP Router periodically transmits HELLO messages using a link-local multicast on each of its interfaces with a hop-limit of 1 (i.e., HELLOs are never forwarded). In these HELLO messages, an NHDP Router announces the IP addresses as heard, symmetric or lost neighbor interface addresses.
An Attacker has several ways of harming this neighbor discovery process: It can announce “wrong” information about its identity, postulate non-existent links, and replay HELLO messages.
The different ways of attacking an NHDP deployment may eventually lead to inconsistent information bases, not accurately reflecting the correct topology of the MANET. The consequence hereof is that protocols using NHDP will base their operation on incorrect information, causing routing protocols to not be able to calculate correct (or any) paths, degrade the performance of flooding operations based on reduced relay sets, etc.
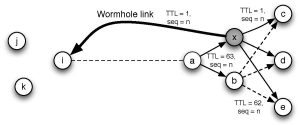
An example of replay attack using TTL/hop-limit field
Related documents:
2016
Herberg, Ulrich; Clausen, Thomas; Yi, Jiazi
Security Threats for the Optimized Link State Routing Protocol version 2 (OLSRv2) Miscellaneous
2016.
@misc{herberg_security_olsrv2,
title = {Security Threats for the Optimized Link State Routing Protocol version 2 (OLSRv2)},
author = {Ulrich Herberg and Thomas Clausen and Jiazi Yi},
url = {https://tools.ietf.org/html/draft-ietf-manet-olsrv2-sec-threats-02},
year = {2016},
date = {2016-05-09},
urldate = {2015-11-20},
keywords = {},
pubstate = {published},
tppubtype = {misc}
}
Yi, Jiazi; Clausen, Thomas H.; Herberg, Ulrich
Security Threats to Simplified Multicast Forwarding (SMF) Miscellaneous
RFC 7985, 2016.
@misc{rfc7985,
title = {Security Threats to Simplified Multicast Forwarding (SMF)},
author = {Jiazi Yi and Thomas H. Clausen and Ulrich Herberg},
url = {https://rfc-editor.org/rfc/rfc7985.txt},
doi = {10.17487/rfc7985},
year = {2016},
date = {2016-01-01},
number = {7985},
publisher = {RFC Editor},
series = {Request for Comments},
abstract = {This document analyzes security threats to Simplified Multicast Forwarding (SMF), including vulnerabilities of duplicate packet detection and relay set selection mechanisms. This document is not intended to propose solutions to the threats described.},
howpublished = {RFC 7985},
keywords = {},
pubstate = {published},
tppubtype = {misc}
}
This document analyzes security threats to Simplified Multicast Forwarding (SMF), including vulnerabilities of duplicate packet detection and relay set selection mechanisms. This document is not intended to propose solutions to the threats described.
2014
Yi, Jiazi; Herberg, Ulrich; Clausen, Thomas
Security Threats for the Neighborhood Discovery Protocol (NHDP) Miscellaneous
RFC 7186, 2014.
@misc{rfc7186,
title = {Security Threats for the Neighborhood Discovery Protocol (NHDP)},
author = {Jiazi Yi and Ulrich Herberg and Thomas Clausen },
url = {https://rfc-editor.org/rfc/rfc7186.txt},
doi = {10.17487/rfc7186},
year = {2014},
date = {2014-04-04},
number = {7186},
publisher = {RFC Editor},
series = {Request for Comments},
abstract = {This document analyzes common security threats of the Neighborhood Discovery Protocol (NHDP) and describes their potential impacts on Mobile Ad Hoc Network (MANET) routing protocols using NHDP. This document is not intended to propose solutions to the threats described.},
howpublished = {RFC 7186},
keywords = {},
pubstate = {published},
tppubtype = {misc}
}
This document analyzes common security threats of the Neighborhood Discovery Protocol (NHDP) and describes their potential impacts on Mobile Ad Hoc Network (MANET) routing protocols using NHDP. This document is not intended to propose solutions to the threats described.
2012
Yi, Jiazi; Clausen, Thomas
Vulnerability Analysis of Relay Set Selection Algorithms for the Simplified Multicast Forwarding (SMF) Protocol for Mobile Ad Hoc Networks Proceedings Article
In: The 15th International Conference on Network-Based Information Systems (NBiS-2012), 2012.
@inproceedings{Yi2012,
title = {Vulnerability Analysis of Relay Set Selection Algorithms for the Simplified Multicast Forwarding (SMF) Protocol for Mobile Ad Hoc Networks},
author = {Jiazi Yi and Thomas Clausen},
url = {http://jiaziyi.com/wp-content/uploads/2016/08/Vulnerability-Analysis-of-Relay-Set-Selection-Algorithms-for-the-Simplified-Multicast-Forwarding-SMF-Protocol-for-Mobile-Ad-Hoc-Networks.pdf
http://ieeexplore.ieee.org/xpl/login.jsp?tp=&arnumber=6354835},
doi = {10.1109/NBiS.2012.48},
year = {2012},
date = {2012-09-01},
publisher = {The 15th International Conference on Network-Based Information Systems (NBiS-2012)},
abstract = {After more than a decade of research and stan-dardization, Mobile Ad Hoc NETworks (MANET) are finding their place in real-world deployments, such as in community, tactical and vehicular networks. Becoming so present in “the real world” also means that MANETs, and the protocols operating them, are affronted with a more hostile environment, where misconfiguration, eavesdropping, and attacks must be addressed. A first step in addressing MANET security is understanding the vulnerabilities of MANET protocols, and how an attacker can exploit these. This paper studies the Relay Set Selection (RSS) algorithms that are commonly used in multicast routing protocol for MANETs, and which are undergoing standardization as part of the Simplified Multicast Forwarding (SMF) protocol, developed within the Internet Engineering Task Force (IETF). Attack vectors for these different RSS algorithms are described, with the purpose of enabling future development of security solutions.},
keywords = {},
pubstate = {published},
tppubtype = {inproceedings}
}
After more than a decade of research and stan-dardization, Mobile Ad Hoc NETworks (MANET) are finding their place in real-world deployments, such as in community, tactical and vehicular networks. Becoming so present in “the real world” also means that MANETs, and the protocols operating them, are affronted with a more hostile environment, where misconfiguration, eavesdropping, and attacks must be addressed. A first step in addressing MANET security is understanding the vulnerabilities of MANET protocols, and how an attacker can exploit these. This paper studies the Relay Set Selection (RSS) algorithms that are commonly used in multicast routing protocol for MANETs, and which are undergoing standardization as part of the Simplified Multicast Forwarding (SMF) protocol, developed within the Internet Engineering Task Force (IETF). Attack vectors for these different RSS algorithms are described, with the purpose of enabling future development of security solutions.
2011
Yi, Jiazi; Clausen, Thomas; Herberg, Ulrich
Vulnerability Analysis of the SMF Protocol for Mobile Ad Hoc Networks Proceedings Article
In: IEEE CPSCom 2011, 2011, (http://ieeexplore.ieee.org/xpl/articleDetails.jsp?reload=true&arnumber=6142260).
@inproceedings{Yi2011c,
title = {Vulnerability Analysis of the SMF Protocol for Mobile Ad Hoc Networks},
author = {Jiazi Yi and Thomas Clausen and Ulrich Herberg},
url = {http://ieeexplore.ieee.org/xpl/login.jsp?tp=&arnumber=6142260
http://www.thomasclausen.net/wp-content/uploads/2015/12/2011-CPScom-Vulnerability-Analysis-of-the-Simple-Multicast-Forwarding-SMF-Protocol-for-Mobile-Ad-Hoc-Networks.pdf},
doi = {10.1109/iThings/CPSCom.2011.63},
year = {2011},
date = {2011-10-01},
publisher = {IEEE CPSCom 2011},
abstract = {If deployments of Mobile Ad Hoc Networks (MANETs) are to become common outside of purely experimental settings, protocols operating such MANETs must be able to preserve network integrity, even when faced with careless or malicious participants. A first step towards protecting a MANET is to analyze the vulnerabilities of the routing protocol(s), managing the connectivity. Understanding how these routing protocols can be exploited by those with ill intent, countermeasures can be developed, readying MANETs for wider deployment and use. One routing protocol for MANETs, developed by the Internet Engineering Task Force (IETF) as a multicast routing protocol for efficient data dissemination, is denoted "Simplified Multicast Forwarding'' (SMF). This protocol is analyzed, and its vulnerabilities described, in this paper. SMF consists of two independent components: (i) duplicate packet detection and (ii) relay set selection, each of which presents its own set of vulnerabilities that an attacker may exploit to compromise network integrity. This paper explores vulnerabilities in each of these, with the aim of identifying attack vectors and thus enabling development of countermeasures.},
note = {http://ieeexplore.ieee.org/xpl/articleDetails.jsp?reload=true&arnumber=6142260},
keywords = {},
pubstate = {published},
tppubtype = {inproceedings}
}
If deployments of Mobile Ad Hoc Networks (MANETs) are to become common outside of purely experimental settings, protocols operating such MANETs must be able to preserve network integrity, even when faced with careless or malicious participants. A first step towards protecting a MANET is to analyze the vulnerabilities of the routing protocol(s), managing the connectivity. Understanding how these routing protocols can be exploited by those with ill intent, countermeasures can be developed, readying MANETs for wider deployment and use. One routing protocol for MANETs, developed by the Internet Engineering Task Force (IETF) as a multicast routing protocol for efficient data dissemination, is denoted "Simplified Multicast Forwarding'' (SMF). This protocol is analyzed, and its vulnerabilities described, in this paper. SMF consists of two independent components: (i) duplicate packet detection and (ii) relay set selection, each of which presents its own set of vulnerabilities that an attacker may exploit to compromise network integrity. This paper explores vulnerabilities in each of these, with the aim of identifying attack vectors and thus enabling development of countermeasures.
2008
Yi, Jiazi
A Survey on the security of MANETs Technical Report
Polytech'Nantes Nantes, France, 2008.
@techreport{yi-manet-security-2008,
title = {A Survey on the security of MANETs},
author = {Jiazi Yi},
url = {http://jiaziyi.com/wp-content/uploads/2016/08/20080330_A_Survey_on_the_security_of_MANETs.pdf},
year = {2008},
date = {2008-03-30},
address = {Nantes, France},
institution = {Polytech'Nantes},
abstract = {ad hoc networks. The purpose of this note is to give a quick review on the security related problems in MANETs, and to answer the question “at the moment, what do we have to deal with the security”. We first introduce the basic concepts of network security, and then come to the security changes and requirements. The key management and secure routing schemes are presented in section 3 and section 4. },
keywords = {},
pubstate = {published},
tppubtype = {techreport}
}
ad hoc networks. The purpose of this note is to give a quick review on the security related problems in MANETs, and to answer the question “at the moment, what do we have to deal with the security”. We first introduce the basic concepts of network security, and then come to the security changes and requirements. The key management and secure routing schemes are presented in section 3 and section 4.

